Các lựa chọn thay thế Docker: 10 lựa chọn thay thế cho ứng dụng SaaS của bạn
Posted by Administrator | 09/10/2025 | Thủ thuật
Các lựa chọn thay thế Docker: 10 lựa chọn thay thế cho ứng dụng SaaS
Zextras has decided to make available and maintain its own version called Carbonio CE, and that is what we will talk about today. The step-by-step guide below will demonstrate how to install and configure the Carbonio CE email server on an EC2 instance in AWS.
An EC2 instance with an Elastic IP.
You also need to have a DNS record.
| Operating System | CPU | RAM | HD | Email Version |
|---|---|---|---|---|
| Ubuntu 20.04 LTS | 4vCPU | 16 GB | 50GB | Carbonio Release 24.3.0 |
External ports (0.0.0.0/0):
Internal port (VPN/IP Static):
First of all, let’s define and create the URL that we will use for the email server.
I will use the domain alfredocastro.com.br, I defined the URL mail.alfredocastro.com.br for the Carbonio CE web portal.
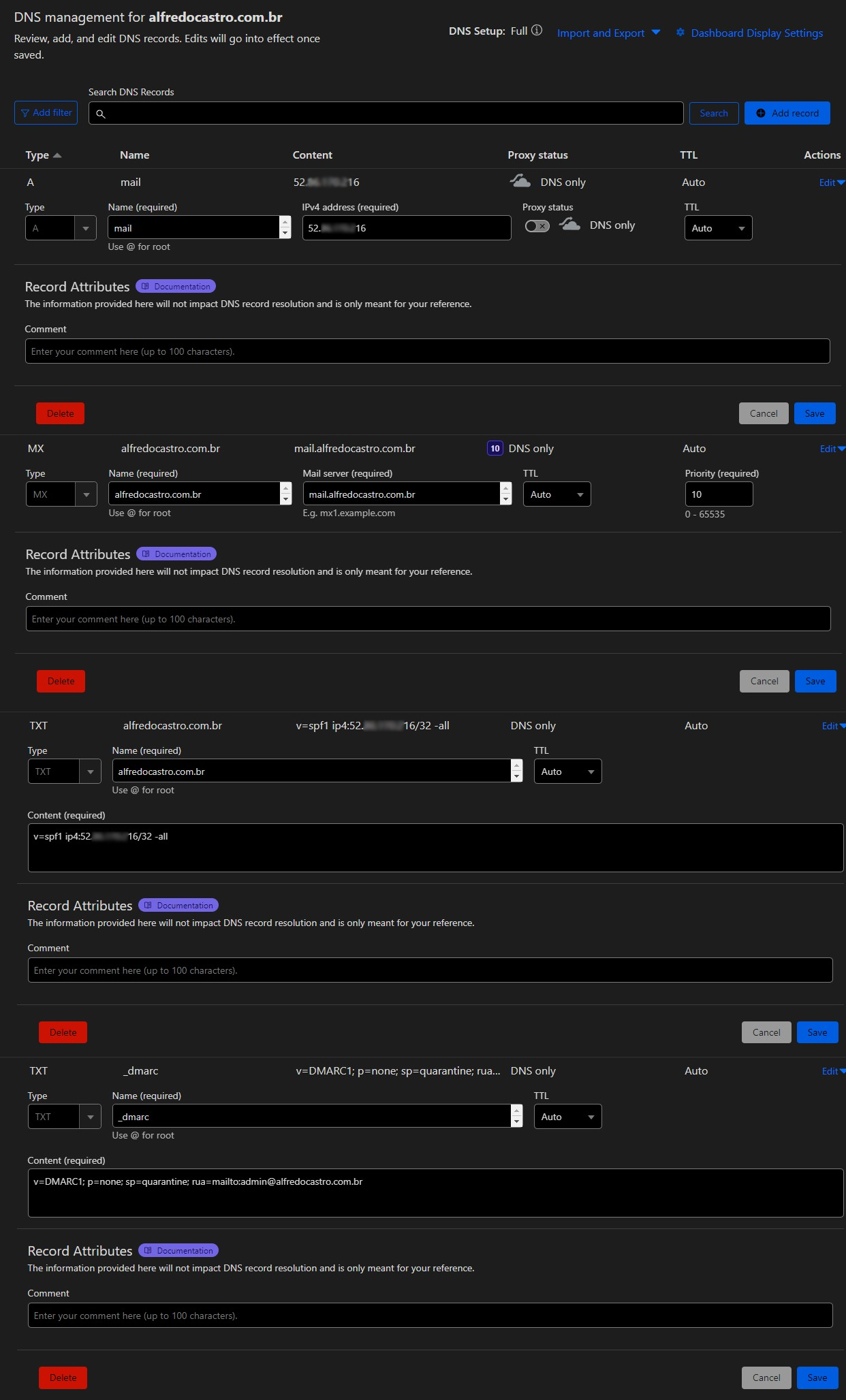
Access your domain’s DNS record manager and create the records below according to your scenario:
| Type | Registration | Value | Observation |
|---|---|---|---|
| THE | 52.XX.XXX.216 | Elastic IP assigned to EC2 | |
| MX | @ | 10 mail.alfredocastro.com.br | URL set for email server |
| TXT | @ | v=spf1 ip4:52.XX.XXX.216/32 -all | Elastic IP assigned to EC2 |
| TXT | _dmarc | v=DMARC1; p=none; sp=quarantine; rua=mailto:admin@alfredocastro.com.br | Email for sending and receiving DMARC compliance reports |
Here’s an example:
To check the propagation of the created record, visit the website: WhatsMyDNS




Note: Before creating a reverse DNS record, you must define a corresponding forward DNS record (type A record) that points to your Elastic IP address (done in the previous step).
Creating a reverse DNS record.
Access the AWS console and look for the “EC2” service.
In the side menu on the left, click on “Elastic IPs”.

Select the Elastic IP and click Actions > Update reverse DNS.

Enter the URL created in the previous step for the email server. Then type update and click the “Update” button.

Access the URL below and fill out the form to request the release of port 25 (SMTP).
https://aws-portal.amazon.com/gp/aws/html-forms-controller/contactus/ec2-email-limit-rdns-request
Email address: email to receive contact from AWS
Use case description: Description of the reason you want to release the SMTP port
Elastic IP address: The IP address assigned to the EC2 instance
Reverse DNS record: The URL you set for Reverse DNS
Then click “Submit”.

You will receive an email confirming your request.

If your request is approved, you will receive another email confirming it.

I used the following text to request the release:
I request the release of the SMTP port for sending emails through the provided EIP below. We will use an EC2 with this EIP to set up a business email server.
To ensure that the EC2 is not used for sending unwanted emails, the following measures will be implemented:
* Email Authentication: Implementation of SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) authentication to verify the authenticity of sent emails.
* Constant Monitoring: Implementation of monitoring tools to identify any suspicious activity or abnormal email volume.
* Responsible Use Policies: Establishment of internal policies to ensure that email sending is done responsibly and in compliance with applicable laws and regulations.
To perform a test, access your EC2 instance and telnet to any email server on port 25. In the example below I used the Gmail server.
telnet smtp.gmail.com 25

First, let’s update the list of packages available in the repositories. Run the following command:
apt-get update

Now let’s change the hostname of the machine. Run the following command:
hostnamectl set-hostname mail

We need to update the /etc/hosts file with the machine’s IP followed by the FQDN and hostname. Run the first command to find out your IP, then change the second command according to your environment:
hostname -I
echo "10.0.2.133 mail.alfredocastro.com.br mail" >> /etc/hosts

Restart the machine using the command below:
reboot
Run the commands below to add the Zextras repository:
NOTE: Go to the Carbonio Community Edition page and fill out the form. You will receive an email with instructions on how to add the repository, similar to the commands below:
cd /tmp
wget https://repo.zextras.io/inst_repo_ubuntu.sh
chmod +x inst_repo_ubuntu.sh
./inst_repo_ubuntu.sh


Now run the command below to install Carbonio CE:
apt-get install service-discover-server \
carbonio-directory-server \
carbonio-proxy \
carbonio-webui \
carbonio-files-ui \
carbonio-admin-login-ui \
carbonio-mta \
carbonio-appserver \
carbonio-user-management \
carbonio-files-ce \
carbonio-files-db \
carbonio-storages-ce \
carbonio-preview-ce \
carbonio-docs-connector-ce \
carbonio-docs-editor \
carbonio-admin-ui \
carbonio-admin-console-ui \
postgresql-12 -y

Run the following command to perform the initial configuration of Carbonio CE:
carbonio-bootstrap

Let’s change the Carbonio CE timezone, type “1” to enter the “Common Configuration” menu:

Type “6” to enter the “TimeZone” menu:

Enter the number corresponding to your timezone, I will set the timezone of “America/Sao_Paulo” number “43”:


Return to the main menu by typing “r”:

Confirm the settings by typing “y”:

Wait until it displays the message “Configuration complete”, and then press “ENTER”:

Now let’s configure Carbonio Mesh, which is necessary to allow communication between Carbonio and its components. Run the command below to perform the configuration interactively:
service-discover setup-wizard
First it will ask for your IP address followed by the network mask, in my example it will be 10.0.2.133/20. Then it will ask for a password for Carbonio Mesh which is used for configuration and management, repeat the password again (for security, it will not show the characters):

Note: If you have lost the password, you can find it in the file /var/lib/service-discover/password (accessible only by the root user).
To complete the Carbonio Mesh installation, run the following command (you will be prompted for a password, enter the password you set in the previous step):
pending-setups -a


Run the commands below to create the Role, Database and the initial file database for Carbonio CE:
NOTE: Change DB_ADM_PWD to a password of your choice in the first and third commands.
su - postgres -c "psql --command=\"CREATE ROLE carbonio_adm WITH LOGIN SUPERUSER encrypted password 'DB_ADM_PWD';\""
su - postgres -c "psql --command=\"CREATE DATABASE carbonio_adm owner carbonio_adm;\""
PGPASSWORD=DB_ADM_PWD carbonio-files-db-bootstrap carbonio_adm 127.0.0.1

Perform a Stop/Start using the commands below:
su - zextras
zmcontrol stop
zmcontrol start

Run the command below to set a password for the Global Admin user (administrator user of the Carbonio CE console accessible on port 6071):
NOTE: Change the domain information as per your environment and change it to a password of your choice.
su - zextras
carbonio prov setpassword zextras@alfredocastro.com.br YOURPASSWORD

NOTE: Run the command logged in as the zextras user (su – zextras).
DKIM, or DomainKeys Identified Mail, is an email authentication method. It helps verify the authenticity of the sender and the integrity of the email message. When an email server uses DKIM, it adds a cryptographic signature to the headers of the sent email. This signature is generated using a private key specific to the sender’s domain.
When the email is received by the destination server, the server verifies this signature using the public key available in the DNS record of the sender’s domain. If the signature matches the email header data, it indicates that the email has not been altered after it was sent by the authenticated sender.
Essentially, DKIM helps combat email spoofing and ensure that emails are authenticated as legitimate. This can help reduce the likelihood of spoofed or malicious emails being delivered to the recipient’s inbox.
To configure, run the following command to generate the DNS record:
NOTE: Change the domain as per your environment.
su - zextras
/opt/zextras/libexec/zmdkimkeyutil -a -d alfredocastro.com.br

In the example above, the following record was generated to be created in DNS:
Tipo: TXT
Registro: 9EEEDFAE-FC33-11EE-9B42-EAD105BED053._domainkey
Valor: v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA5IYCXNy92oQdyTDrXAIfDFz/fHzmNdeqhgSeErR/m0SYDguQKeb7c19zr4imctX2a6HdzV1W5c8w90jvbvKYGUuBOBhSA/APx0DEa+DxV59+D173PE/iKpDuAIBajWyXT+oVH9JX6iCg33Jk4ghEakZ4jz+NsSkVJ3rwUIHvBWnfb7BNF5MPnQ18O9YHvS3POdldIdIme/JHCuew3k/biXIhZxVE9zg2YXwq1AjxCo24jqtDIUhG26koAeSguDDXremk3hyzEG4qKLnF47gdbDSijBBllAMV3CVzqBhBuVOV3gNA1ifGtiAUXH3YHQJeYFqy2yld8oZlqFozuSXzFQIDAQAB
Access your domain’s DNS record manager and create the above record according to your scenario:
Here’s an example:

To check the propagation of the created record, visit the website: WhatsMyDNS

Zextras has introduced a simplified and improved way to configure Let’s Encrypt SSL certificates via the Web Console. With this update, you can now easily deploy certificates for a single domain or multiple domains.
To configure Let’s Encrypt, you need to have the certbot package, run the following command to check if it is installed:
dpkg -l | grep carbonio-certbot

Check your server’s zimbraReverseProxyMailMode mode. By default it is set to https, run the following command:
NOTE: Change the URL as per your environment
su - zextras -c "carbonio prov gs mail.alfredocastro.com.br | grep -i zimbraReverseProxyMailMode"

For certbot to work, we need to change the zimbraReverseProxyMailMode mode from https to redirect, run the commands below to make the change:
NOTE: Change the URL as per your environment
su - zextras -c "carbonio prov ms mail.alfredocastro.com.br zimbraReverseProxyMailMode redirect"
su - zextras -c "zmconfigdctl restart"
su - zextras -c "carbonio prov gs mail.alfredocastro.com.br | grep -i zimbraReverseProxyMailMode"

Log in to the Carbonio CE Administration Console, use the username zextras@alfredocastro.com.br :
NOTE: https://mail.alfredocastro.com.br:6071/ – change the URL according to your environment

Click on “Domains” in the left side menu:

Select the desired domain:

Click on “Virtual Hosts & Certificates”:

Enter the URL you configured on your mail server and click “ADD”:

Click “SAVE”:

Click on “UPLOAD AND VERIFY CERTIFICATE”:

Change “Certificate Type” to “I want to use a Let’s Encrypt (longChain) certificate” and then click “GENERATE CERTIFICATE”:

You will see a green notification saying “The System is processing your certificate generation request. It will send the result to the Global and Domain notification recipients.”, Carbonio CE will request the certificate.

If everything goes well, you will receive two emails confirming the completion of the request. Access the URL of your email server and log in with the user zextras@alfredocastro.com.br :



Finally, run the command below to restart Carbonio CE and complete the SSL Certificate installation:
su - zextras -c "zmcontrol restart"

I hope I’ve helped! If you have any questions, don’t hesitate to contact me.
Liên hệ ngay với OceanTech-Group để thiết kế hệ thống trơn chu chuẩn bảo mật cho doanh nghiệp của bạn!

Ý kiến đóng góp