GIỚI THIỆU NỀN TẢNG ẢO HÓA VMWARE NSX-T
Posted by Administrator | 04/02/2026 | Thủ thuật
NSX-T là gì? Tìm hiểu nền tảng ảo hóa mạng VMware NSX-T – OceanTech Group
Initial setup of Microsoft Intune MAM/MDM
Microsoft Intune, previously known as Windows Intune, is a part of Microsoft Cloud-based Mobile Device Management (MDM), Mobile Application Management (MAM), and Windows PC Management Solution. No on-premise infrastructure is required for using this service from Microsoft, and it can be easily managed using Microsoft Intune’s admin center URL: https://intune.microsoft.com.
Intune is included in Microsoft Enterprise Mobility + Security (EMS) and Integrates with Microsoft 365, Entra ID, and Azure Information Protection (AIP).
Microsoft Intune is included in the following licenses:
►Microsoft 365 E5 ► Microsoft 365 E3 ►Enterprise Mobility + Security E5 ► Enterprise Mobility + Security E3 ►Microsoft 365 Business ►Microsoft 365 F3 ►Microsoft 365 Government G5 ►Microsoft 365 Government G3
Before setting up Intune for your Client, please check the Supported OS and Browsers in Intune.
Sign up On the below Intune Portal (you can get a 30-day free trial of Intune when you sign up) Sign-up for Intune.
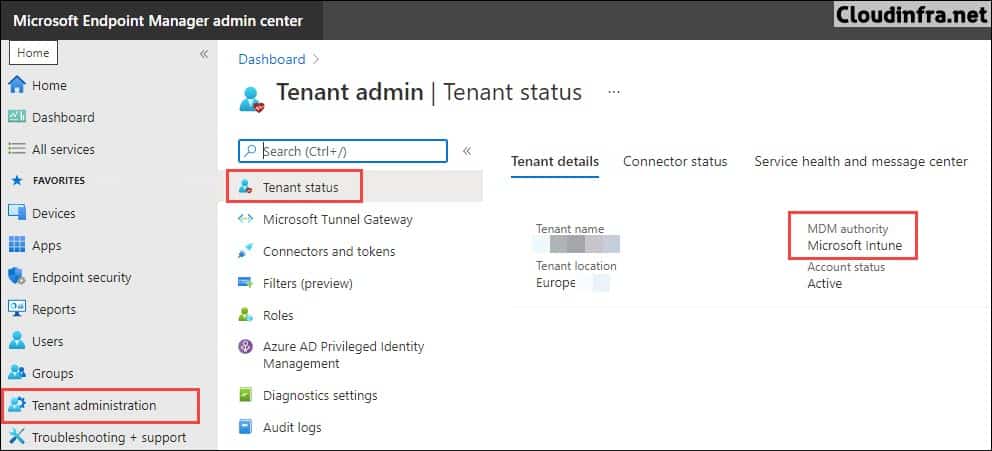
First, you must configure mobile device management (MDM) authority. A setting called MDM Authority determines how and where you manage your devices. It is a pre-requisite and a part of the initial configuration to set the MDM Authority before you can enroll any device to Intune.
Once you have set the MDM Authority, you can check its status as shown below:
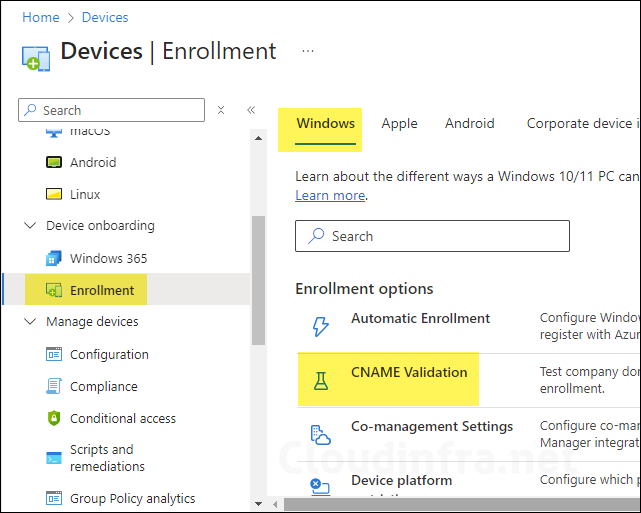
After setting up MDM Authority, you can setup Device Enrollment. I will first go through the Apple enrollment process, Android enrollment, and Windows enrollment.
These do not have to be in order; you can configure enrollment of devices in any order you like. However, for this configuration, we will start with Apple enrollment first.
Configure Apple MDM Push Certificate to enroll Apple devices into Intune. You can refer to the step-by-step guide on Create Apple MDM Push Certificate for Intune.
For the configuration of Android Enrollment, we must first link organization’s Google Play account to Intune. You can refer to the step-by-step guide on configuring Android Enrollment On Intune Admin Center.
To manage Windows devices using Intune, devices must first be enrolled into Intune. Both personally-owned and corporate-owned devices can be enrolled. Let’s check the steps:
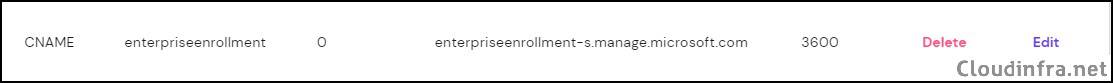
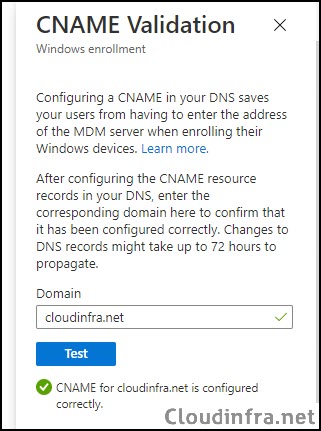
| Type | Name | Points to | TTL |
|---|---|---|---|
| CNAME | enterpriseenrollment.cloudinfra.net | enterpriseenrollment-s.manage.microsoft.com | 3600 |
| Important |
|---|
| If the company uses more than one UPN suffix, you need to create one CNAME for each domain name and point each to EnterpriseEnrollment-s.manage.microsoft.com. |
To configure Automatic enrollment of Entra joined devices into Intune, follow below steps:
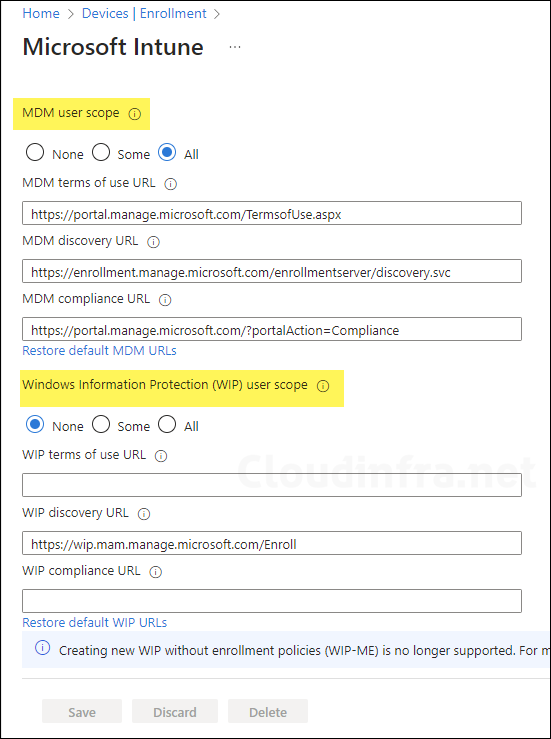
Configure MDM User Scope: Specify which users devices should be managed by Intune. These Windows 10/11 devices can automatically enroll for management with Microsoft Intune. Select All.
Configure Windows Information Protection (WIP) user scope: None
For more Information on Automatic Enrollment: https://learn.microsoft.com/en-us/mem/intune/enrollment/windows-enroll#enable-windows-automatic-enrollment
You can control which devices can enroll in Intune by setting up device enrollment restrictions. There are two main types of restrictions you can configure:
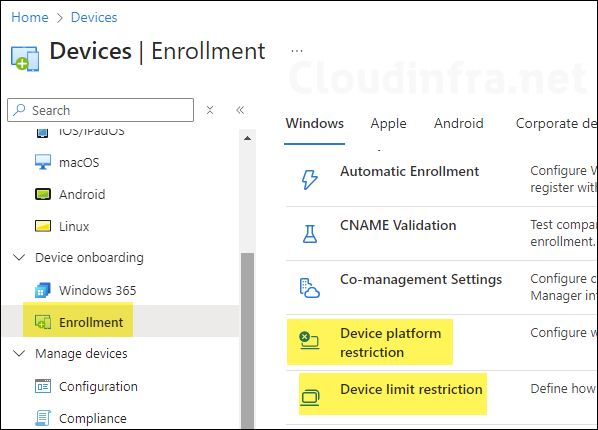
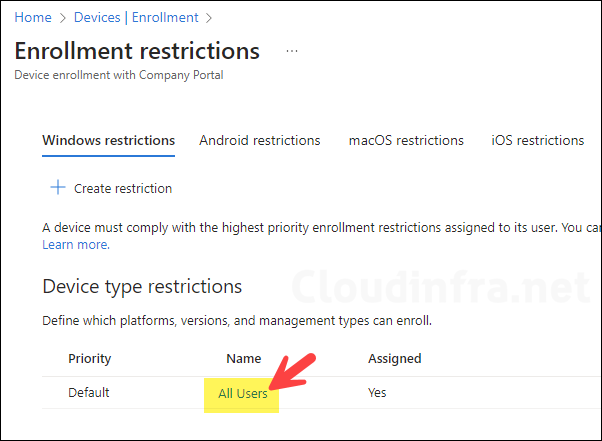
You’ll find a default policy already there when you go to the Device Platform restrictions page. This policy applies to All users. You can change this default policy or create a new one if needed.
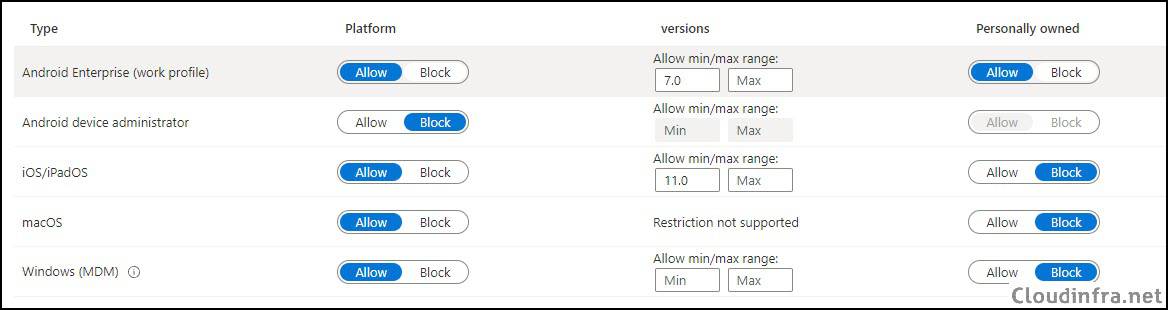
We will modify and configure the default policy according to the business requirements. Overall, we will be blocking iOS, macOS and Windows Personal devices, Only Corporate devices will be allowed.
You can also create a custom device platform restriction policy for each platform and assign it to All users. To create a custom device platform restriction policy, Go to Intune admin center > Devices > Enrollment > Device type restriction > Create restriction.
| How a device is classified as Corporate Device in Intune |
|---|
| At the time of enrollment, Intune automatically assigns corporate-owned status to devices that are:
>> Enrolled with a device enrollment manager account (all platforms) After enrollment, you can change the ownership setting between Personal and Corporate. |
| Source: Microsoft |
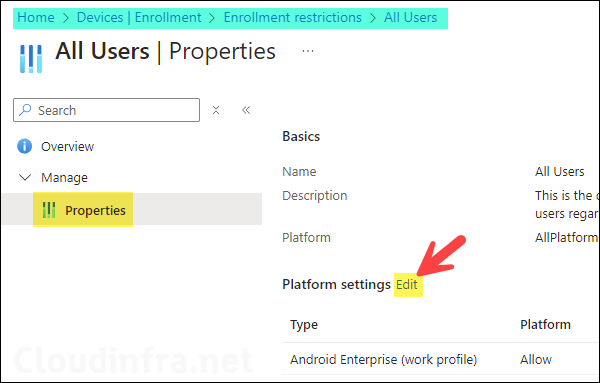
Go to Intune admin center > Devices > Enrollment > Device type restriction > Click on All Users to open Default policy settings.
Create a Device compliance policy for each platform: Android, iOS, macOS, and Windows. Follow below steps to create a Device compliance policy:
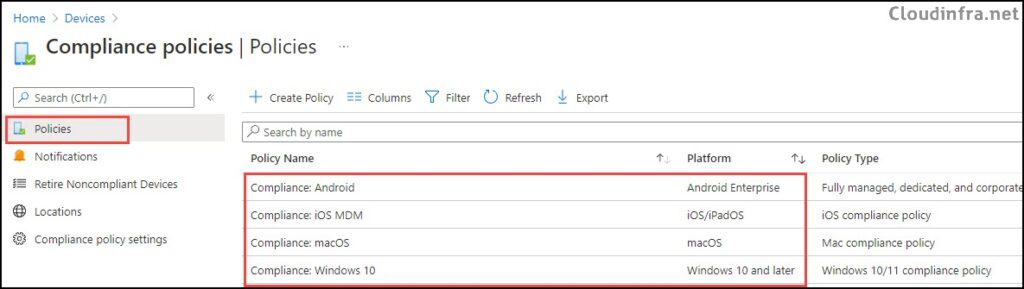
You can create a device configuration profile to make changes to device settings and configure certain features on managed devices. You can use available Templates or Settings Catalog to configure and deploy device settings via the Intune admin center.
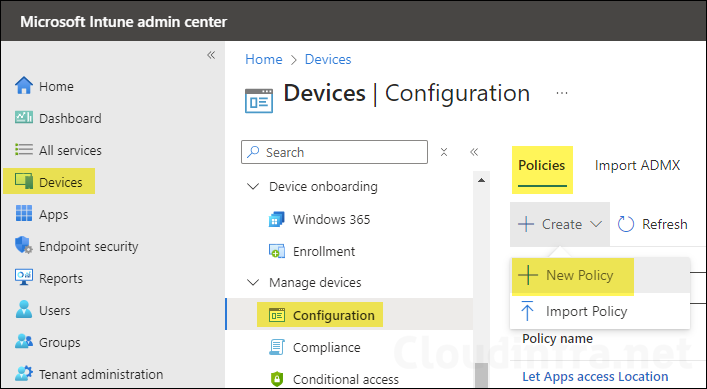
To create a device configuration profile. Sign in to the Intune admin center > Devices > Configuration > Create > New Policy. I have created several blog posts to configure various settings on Windows and macOS devices. You can refer to any blog posts below to understand the process step-by-step.
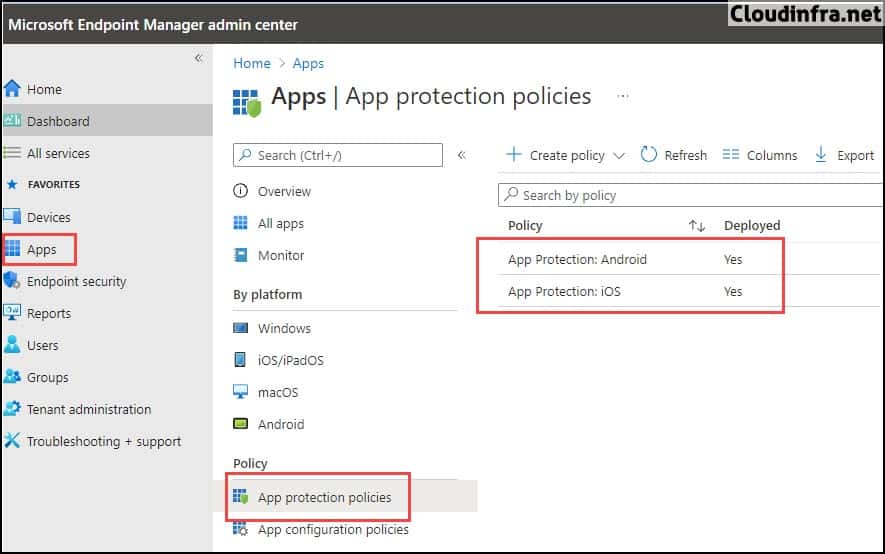
You can create App protection policies for BYOD devices to manage applications and protect the organization’s data. Some of the use cases of App protection policies are:
To create an App protection policy, Go to Intune admin center > Apps > App Protection policies > Create policy. You can create an App protection policy for each platform and Include the apps you want to protect on BYOD devices.
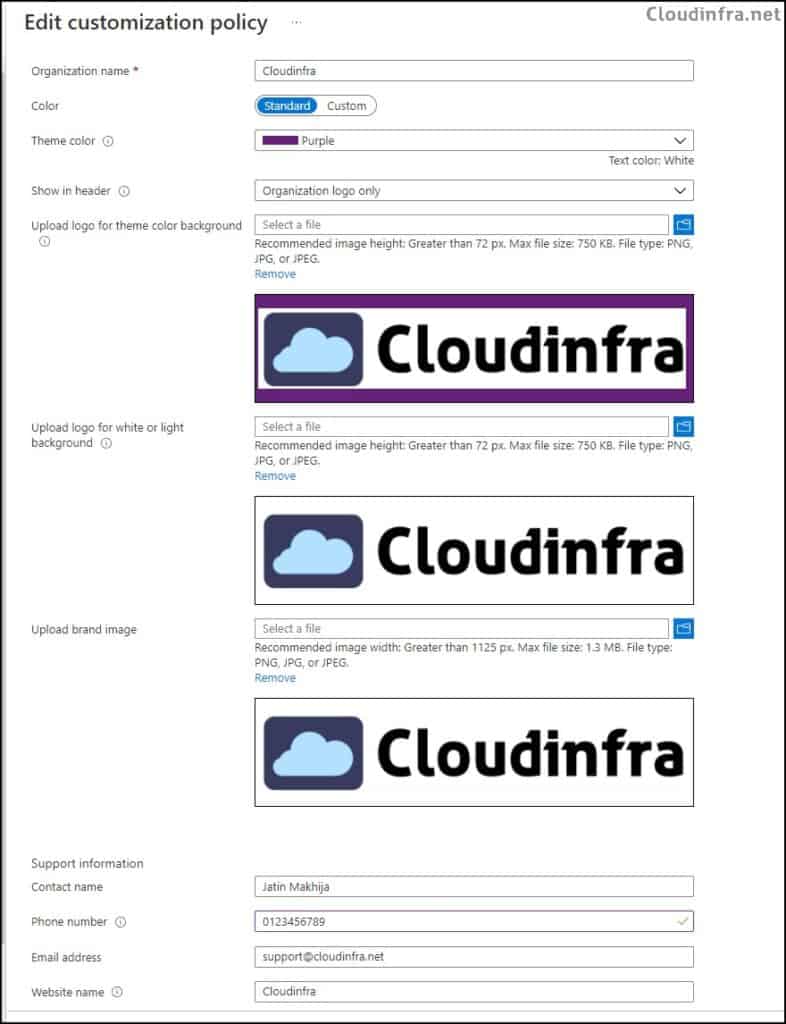
You can personalize the user experience by adjusting the look of the company portal. This includes adding your company’s logo, choosing a theme color, setting a background, and providing contact details for your helpdesk and company website.
To configure the Customization policy, follow below steps:
For more details on customizing and best practices, refer to the following article on the Microsoft website: Link to Microsoft Article.
You can add apps from the iOS Store, Managed Google Play, or create custom Windows apps (Win32) for deployment. Let’s look at how to add, assign, delete, and monitor apps in Microsoft Intune. Below are some application deployment examples:
You can include iOS Store apps and manage them through the Intune admin center. Follow this step-by-step guide to learn how to manage iOS Store apps using Intune.
You can integrate and manage Google Play Store apps through the Intune admin center. Here’s a step-by-step guide to help you manage Google Play Store apps using Intune.
Setting up a Work Profile effectively manages Bring Your Own Device (BYOD) Android devices. Follow this step-by-step guide to learn how to set up a Work Profile on an Android phone.
You can enroll macOS devices owned by users (BYOD) into Intune with ease. This process begins with installing the company portal app on the macOS. Here’s a step-by-step guide on how to enroll macOS devices in Intune.
If you encounter any problems during macOS enrollment, refer to my blog posts that address macOS enrollment issues and macOS Intune Logs collection.
In this blog post, we covered the initial setup of Intune from the ground up. All the policies and configuration settings can be tailored to your specific needs. It’s essential to test these policies on a few devices. I hope your setup goes smoothly without any problems.
Liên hệ ngay với OceanTech-Group để thiết kế hệ thống trơn chu chuẩn bảo mật cho doanh nghiệp của bạn!
